Table of contents
No headings in the article.
What is AWS Security?
AWS security service assists you in safeguarding sensitive data and information while also meeting compliance and confidentiality standards.
AWS enables you to automate tedious security processes so you can concentrate on growing and innovating your company.
Furthermore, you only pay for the services you utilize.
Types of AWS Security:
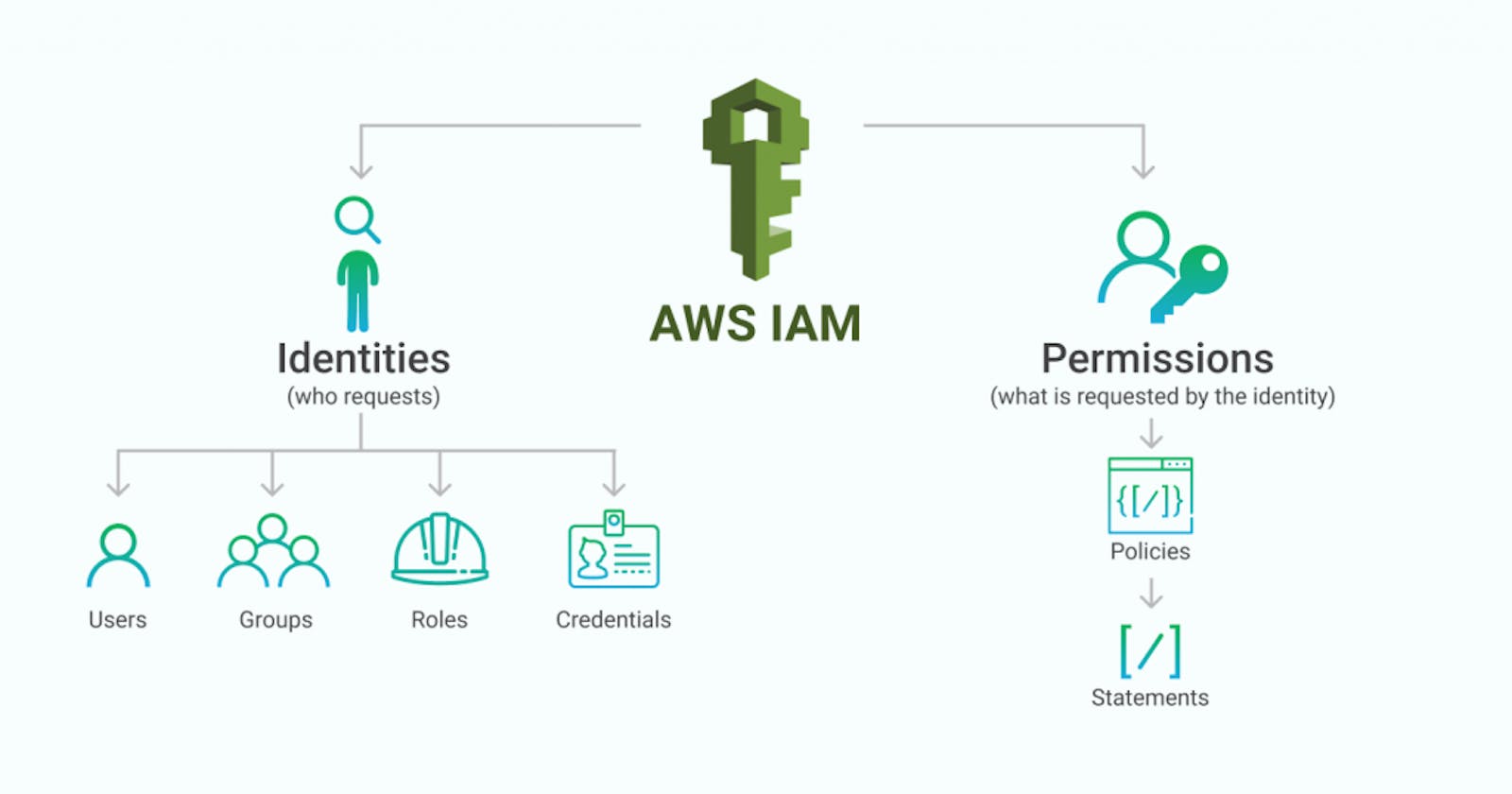
IAM (Identity and Access Management)
Amazon GuardDuty
Amazon Macie
AWS Config
AWS CloudTrail
What is IAM?
- AWS Identity and access management(IAM) safeguards accesses to AWS services and resources and to create and manage AWS user and groups and use permissions to grant or deny access to AWS services.
Benefits of IAM:
- Scale Securely with Superior Visibility and Control.
Control over your data storage.
Fine Grain Identity.
Continuous Monitoring for real time security information.
- Automate and reduce Risk with deeply integerated services
Reduced Human config error
Wide variety of deeply integrated solutions.
- Inherit the Most Comprehensive security and compliance controls
regularly achieves third-party validation for thousands of global compliances.
helps you meet security and compliance standards.
- Build with the Highest Standards for privacy and data security.
Build on the most secure global infrastructure.
ability to encrypt data, move it, and manage retention.
Working of IAM:
- Prinicpal
An action on an AWS resource can be performed by a principal.
A user or a role can be a principal.
- Authentication
It is a process of conforming identity of the prinicpal trying to access an AWS product.
To authenticate from console, you must provide your credentials or required keys.
- Request
- When a prinicpal attempts to access the AWS Console, API or CLI, he sends a request to AWS.
- Authorizations
- Here IAM uses information from the request context to check for matching policies and determine whether to allows or deny the request
- Actions
After authentication and authorization of the request, AWS approves the action
Using this, you can either edit, or delete or even create a resource.
- Resources
A set of actions can be performed in a related resource of AWS account.
Suppose, a request is created by a user to perform an unrelated action then the request gets denied.
Components of IAM:
AWS IAM users are AWS entities that represen the person or application that interacts with AWS.
AWS users have a name and credentials. A user's "friendly name", which is the name you gave them they were formed.
The root user of AWS account is not the same as an IAM user with administrator access.
A set of IAM users is referred to as an IAM user group.
User groups allow you to specific permission for many users, making it easier to manage those user's permissions.
In a resource-based policy, a user group can't be designated as a Prinicpal.
A user group is a technique to apply policies to a group of people all at once.
An IAM role, like IAM user, is an AWS Identity with permission policies that govern what the identity can and cannot do in AWS.
There are no long-term credentials connected with a role. Instead, when you take on a role, you're given temporary security credentials for the duration of your role session.
Users, applications, and services that don't ordinarily have access to your AWS resources can be given access through roles.
Policies are created and linked to IAM identities (users, groups of users, or roles) or AWS resources to manage access in AWS.
A policy is an object that defines the rights of an identity or resources when it is associated with it. AWS examines them when it is associated with it. AWS examines them when an IAM prinicpal (user or role) submits a request.
The policy permission decide whether the request is approved or rejected. Most policis are saved as JSON document on AWS.
Features of IAM
Shared access to your AWS account.
Granular permissions
Secure access to AWS resources.
MFA (Multi-Factor Authentication)
Identity Fedration.
Free to use.
PCI DSS compliance.
Password policy.
I hope you find this useful. Thank you for reading this article !!!